Email Security | Phishing | Email Fraud | Malware Attacks | Ransomware | Spoofing
Global business is interspersed with a diversity of industrial sectors, united by a single, common communication thread that is key to any business: email connectivity.
In 2018, the estimated number of emails sent and received were 280 billion, daily.
That’s 11,666,666,666 per hour.
194,444,444 per minute.
3,240,740 per second.
Whichever way you look at it, that’s a lot of email!
What’s in an Email?
As the world turns fully digital, email has become the foundation of our daily communications. From hospital appointments to job applications; our emails include bank details, medical records, sales contracts, tax information, legal documents, and everything in between. It seems we love sharing information, however there are plenty of unscrupulous individuals and companies out there who would love to get their hands on it as well.
On a personal level, the amount of information we are happy to share through email not only leaves us open to the inconveniences of spamming, phishing, and computer viruses, but also to full-scale identity theft.
As far as businesses and organizations are concerned, if the right information gets into the wrong hands there can be devastating consequences. High-profile data breaches are becoming increasingly common, and hackers are constantly trying to access sensitive company information that can directly affect any entity’s bottom line.
Top EIGHT Threats to Email Security
To better protect against email security threats, it’s important to know what the biggest threats are. Here’s a short list of some of the most common or dangerous threats to an organization’s email security:
- Phishing Attacks
Email phishing is a security attack used by cybercriminals who use it in an attempt to steal sensitive business information. This type of data includes usernames and passwords of CEOs, CFOs and other senior management, details about financial accounts or valuable information which can be sold to competitors.Did you know that there are at least 3.4 billion fake emails sent out as part of a phishing scam every single day?According to statistics cited by techradar.com, that’s the minimum. This is a sobering statistic, one that should highlight the importance of email security. Worse yet, phishing attacks are becoming increasingly sophisticated, leading to new types of attacks that are getting better at tricking people. - Spear Phishing Attacks
This is the name for a specific subset of phishing attacks that are highly customized and targeted to a specific individual or organization. These spear phishing attempts often mimic the tone and style of an organization’s official communications, incorporate copies of the organization’s letterhead and logo, and use an email domain that is similar to the one the organization uses – one that might pass a cursory inspection, except for having one additional letter/number or having two letters/numbers transposed. These social attacks are a major threat because they can trick even experienced and knowledgeable individuals into making mistakes. - Spoofing
A spoofing email is a strategy used during spam and phishing attacks. By falsifying the header of an email to make it seem like its coming from inside the company, an attempt is made to confuse employees to provide sensitive information or in some cases even bank transfers.While due diligence is the best method of dealing with spoofing attacks, companies should also look to software which improves email security for enterprises. - Malware
Malware, or malicious software, is a virus which contains coding programmed to attack and harm data, tech equipment or entire systems. Trojans, viruses, spyware, worms, adware, botnets and ransomware are all types of malware, but so far, the list includes 796 million registered malware programs.In most cases, malware is via email during phishing and spam attacks. During an attack, multiple emails with a virus are sent across an enterprise. After being opened, malware infects the system and cause damage to it.Teaching company employees is the first line of malware defense. If someone receives an email from an unknown source and with a large attachment, it is best they delete the mail immediately.

- Ransomware
Ransomware is a specific type of malware which attacks the entire computer system and blocks access to users until the financial demand (ransom) is paid to the perpetrator. Threats to email security like this usually happen during other large-scale attacks when multiple users are targeted inside the company. - Weak Email Passwords
One way that some attackers may try to hijack email accounts is by simply guessing the account’s password. Accounts that have weak or easy to guess passwords can be hijacked without the user’s knowledge – then get used to send out phishing attack emails from a legitimate company address. According to the 2019 DBIR, about 80% of attacks we are compromised due to weak passwords and credentials. As organizations accordingly invest in passwords managers, it remains clear that their biggest issue continues to be one that makes their postures weaker. - Malicious Download Links and Attachments
Many phishing attack emails include links or attachments that are primed with malware. The specific effects of this malware can vary depending on the type of malware that is downloaded. For example, ransomware will encrypt all of the data on the affected computer’s drive (or on the drives of every computer/database on the network), then demand a payment (i.e. ransom) in return for the encryption key. Meanwhile, other malware programs may simply sit on the infected device and passively collect information (such as login credentials or financial data), then transmit that data to an offsite server for the cybercriminal to collect later. - Directory Harvest Attacks
A directory harvest attack (DHA) is an email threat carried out by spammers which has a goal of accessing the email database attached to a company domain. Although simple tactics like a dictionary attack are used, DHAs target both personal and commercial information, inflicting massive damage across a large enterprise.
The Importance of Email Security
A full 45 percent of IT executives cite malicious insider attacks as one of the email security risks they are most ill-prepared to cope with. A recent study by Enterprise Management Associates (EMA) found that insiders were responsible for 60-percent of leaks. This breaks down into:
- 20% of employees who accidentally share or expose data;
- 20% of employees that are deceived into disclosing information through social engineering, malware or phishing;
- And 20% of employees who maliciously leak company information, or who are compensated for its theft.
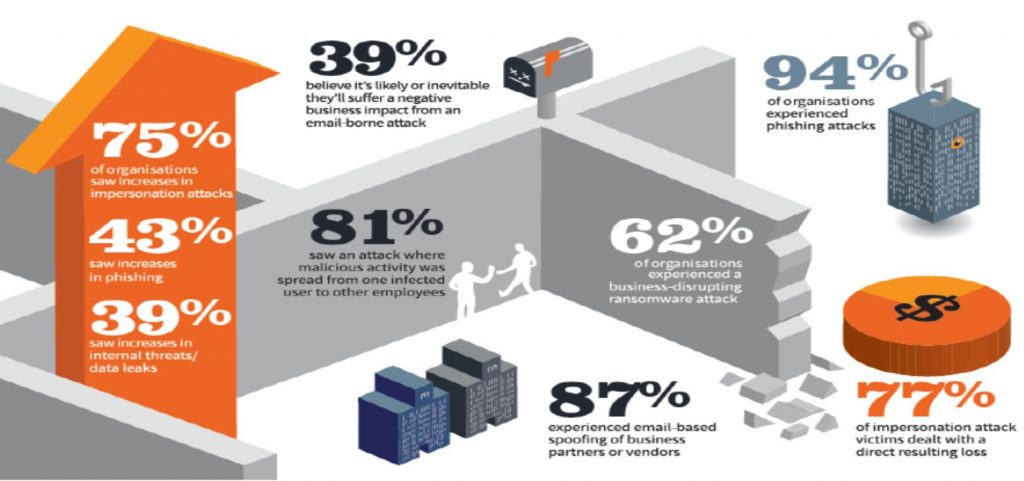
Email security is tough. It always has been. Bad actors are constantly finding innovative ways to evade detection, successfully breach defenses and monetize their attack. Cyber security is an arms race and every cyber security professional knows that no single security control can ever be 100% effective. This is because no one can foresee what the next innovative evasion tactics will be, so we invest in multiple layers of controls.
One of the most important security layers is to protect against email threats.
Find FIVE reasons why you need better email security, or put another way, why your current email security might be failing.
- Email Security is not a Commodity
More than 90% of attacks start with an email. This is a well-known, often quoted statistic. What is less well known is that spend on email security accounts for a little over 5% of total global security software spend. This 5% includes secure email gateway products and services and is clearly completely out of proportion to the threat. There is an incorrect belief that email security is a commodity and many organizations rely on the free email security that comes bundled with their email platform. This is despite an abundance of evidence from independent test labs that shows that the detection efficacy afforded by these services is often lacking. - Malicious domains and websites rapidly appear and disappear
Around 200,000 new domains are registered every day and about 70% of these are malicious or suspicious. Phishing sites can come online for just hours. It is impossible for any cyber security company to track every new malicious domain and website, so if your email security product just looks up any URLs in emails against a list of known malicious ones, the likelihood of that list being up to date is extremely remote.
Weaponizing URLs in an email a few minutes after sending it is a tactic that has been around for many years, so even performing a full analysis of the URL’s target web page on receipt will likely be ineffective. Your email security must re-write URLs before delivery and check them each and every time the recipient clicks them. The URL should be followed to its final destination and the content analyzed, and the security must understand and overcome the many tactics that will be used to evade detection. - Phishing kits are driving the increase in phishing attacks
The availability of phishing kits and phishing as a service has democratized phishing, making it easy for any non-technical cyber criminal to launch a phishing attack. A kit contains everything someone needs to launch a phishing campaign and can be purchased for as little as $99, with additional costs for mailer services. With phishing as a service, a bad actor simply gives email addresses to the service provider and enters into a revenue sharing model with them. Evasion tactics play a part in phishing kits too – the more expensive the kit, the more tactics it will include to help the phish evade detection by the target’s email security. - Attackers are successfully compromising email accounts
The goal of many email attacks is to steal credentials. A Tech Validate survey reported, in the previous 12 months, over half of respondents had suffered from threats caused by attackers compromising their users email accounts. The ubiquity of cloud services has resulted in the traditional network perimeter disappearing. To access your applications and information, an attacker no longer has to first gain access to your network.
In much the same way that the success of Windows made it a target for malware, the success of Office 365 has resulted in it becoming a major target for those wishing to steal business login credentials. Many phishing kits are designed to steal Office 365 credentials. In a 262 day period Microsoft was the top targeted brand with 62 kit variants found across 3,897 domains. Once inside a user’s Office 365 account, an attacker can set up rules to divert and monitor emails, understand your business, your customers and your business partners. Clearly, if your email security is just monitoring inbound emails at the email perimeter, you have no visibility of this. - Evasion tactics make detection difficult
The first polymorphic viruses, created around 1990, were designed to change slightly to evade detection by signature-based AV engines. Today, malware attempts to evade detection by even the most advanced sandboxes, by understanding that it might be executing in a sandbox and exhibiting very different behaviors that it would if executed on a laptop. Phishing emails use many tactics to evade detection too. Attackers impersonate domains, senders and websites, and use social engineering tactics to trick the recipient into disclosing their credentials or other sensitive information.
How Mimecast Helps Organizations to keep their Emails Secure
Mimecast is a cybersecurity provider that helps thousands of organizations worldwide make email safer, restore trust and bolster cyber resilience. Email is the number one threat vector facing organizations today, and Mimecast’s fully-integrated, cloud-based services protect customers across the globe from incidents that typically start with email, including advanced cyberattacks, data loss, downtime, and human error.
Mimecast services protect millions of employees at over 36,000 customers across a broad set of vertical markets in over 130 countries. Integrating with enterprise email platforms including Microsoft Exchange and Office 365, as well as Google, their services process more than two billion emails per day.
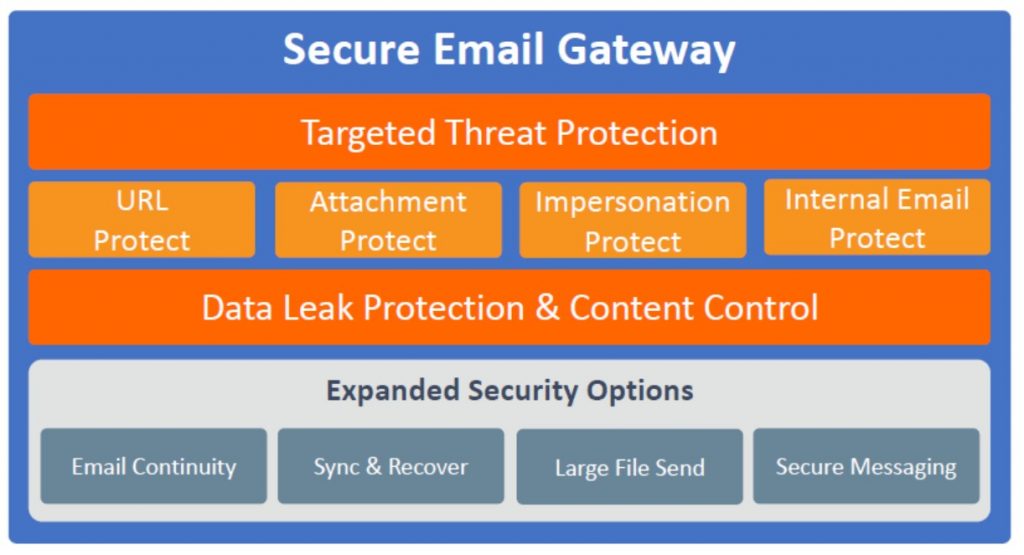
Mimecast Email Security services provide multi-layered protection against known and unknown email security issues. As a cloud-based subscription service, Mimecast simplifies enterprise email management with an all-in-one solution eliminating the need to purchase, deploy and manage multiple security solutions from multiple vendors. With sophisticated intelligence and multi-layered detection engines, Mimecast brings best of breed protection against a host of email security issues including malware, spam, advanced threats and zero-day attacks.
Let’s have a look at the various solutions Mimecast provides in order to secure your emails below:
- MIMECAST INTERNAL EMAIL PROTECT
Mimecast Internal Email Protect applies best-practice security inspections to internal and outbound email traffic, allowing organizations to monitor, detect, and remediate security threats that originate from within their email systems. A 100% cloud-based service, it includes scanning of attachments and URLs, as well as content inspections for violations of data leak prevention policies. Internal Email Protect is a component of Mimecast’s Targeted Threat Protection service and integrates seamlessly with Mimecast’s full suite of security solutions.

Mimecast Internal Email Protect both continuously rechecks previously delivered inbound files to identify malware that wasn’t initially detected and allows you to automatically or manually reach back in to users’ inboxes to remove unsafe or undesirable emails.
By applying world-class security protocols to all organizational email, Mimecast helps you reduce both cost and complexity while expanding your ability to safeguard employees, intellectual property, customer data, and your organization’s brand reputation.
- MIMECAST CONTENT CONTROL & DATA LOSS PREVENTION (DLP)
The Mimecast Content Control & DLP is a cloud service that protects your organization from data leakage via email including, intellectual property, customer details and other sensitive information. Email content and secure communication policies can be created and applied to outbound traffic in real-time.
Content Control and Data Leak Prevention use keywords, pattern matching, file hashes and dictionaries to scan all email and attachments to prevent malicious and accidental data leaks, blocking and quarantining suspected leaks for review by administrators.
- MIMECAST TARGETED THREAT PROTECTION (TTP)
Mimecast TTP is a suite of services delivering inspection of inbound, outbound and internal emails to help detect and fight phishing, ransomware, impersonation attempts, malicious URLs, weaponized attachments, and internal compromise.

Mimecast’s Targeted Threat Protection – URL Protect uses multiple, sophisticated, detection engines and a diverse set of threat intelligence sources to protect email from malware, spam, phishing, and targeted cyberattacks delivered as a 100% cloud-based service.
Mimecast’s Targeted Threat Protection – Attachment Protect provides comprehensive protection against both known and unknown threats through a multi-layered approach leveraging static file analysis, safe-file conversion and behavorial sandboxing for advanced protection from email-borne malware.
Mimecast’s Targeted Threat Protection – Impersonation Protect provides instant and comprehensive detection against the latest malware-less social engineering-based email attacks, protecting organizations from attackers exploiting their name and reputation, well-known Internet brands, and third-party organizations they may work with.
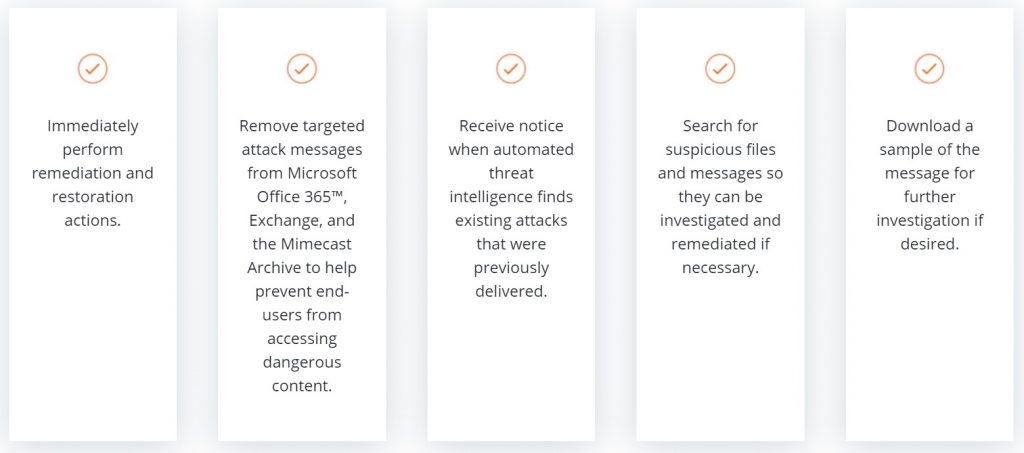
- MIMECAST THREAT REMEDIATION
Was a malicious email forwarded to the entire company?
Sensitive data sent to the wrong person?
Act fast with Mimecast Threat Remediation. As IT professionals (and human beings), we expect mistakes to happen. The key is minimizing damage when they occur.
With Mimecast’s Threat Remediation capabilities, you can quickly identify the source of problems and take action on the spot to help stop the spread of a cyber-attack, protect sensitive data, and minimize damage. You can thereby help prevent the spread of malware both internally and to external parties by remediating malicious files or messages post-delivery.
The key capabilities of Mimecast’s Threat Remediation are:
Benefits of Mimecast Unified Email Management
Mimecast’s all-in-one solution enables you to:
- Streamline email infrastructure with a centrally-managed cloud solution eliminating the need for multiple single-purpose technologies.
- Reduce overhead by avoiding the need for more on-premises equipment.
- Improve the user experience by ending mailbox size restrictions, offering fast access to archives and delivering continuous access to email.
- Gain greater control of email by setting security and data retention policies from a single administrative console.
Why Email Security can no longer be ignored
Email security issues are some of the biggest threats to your organization’s productivity and profitability. From malware and viruses to advanced threats like email phishing, email security issues can lead to breaches that cost millions of dollars in lost business and damage to your reputation. Companies whose email security systems could not stop some new email threat are all over the news.
Mimecast Email Security services provide multi-layered protection against known and unknown email security issues. As a cloud-based subscription service, Mimecast simplifies enterprise email management with an all-in-one solution eliminating the need to purchase, deploy and manage multiple security solutions from multiple vendors. With sophisticated intelligence and multi-layered detection engines, Mimecast brings best of breed protection against a host of email security issues including malware, spam, advanced threats and zero-day attacks.
To figure out how Mimecast can help your business eliminate email related threats, please get in touch with our experts today
Author